Cyber Security
At a Glance
Invaluable insights on cyber security to safeguard your digital presence. Explore, learn, and fortify your online world.
In an era dominated by interconnected systems and a digital landscape that knows no bounds, the significance of network security cannot be overstated. As businesses and individuals alike continue to embrace the digital age, the need for robust measures to protect sensitive information and ensure the integrity of networks has become paramount.
This blog explores the pivotal role of network security in safeguarding digital assets and maintaining the integrity of cyberspace.
Understanding Network Security
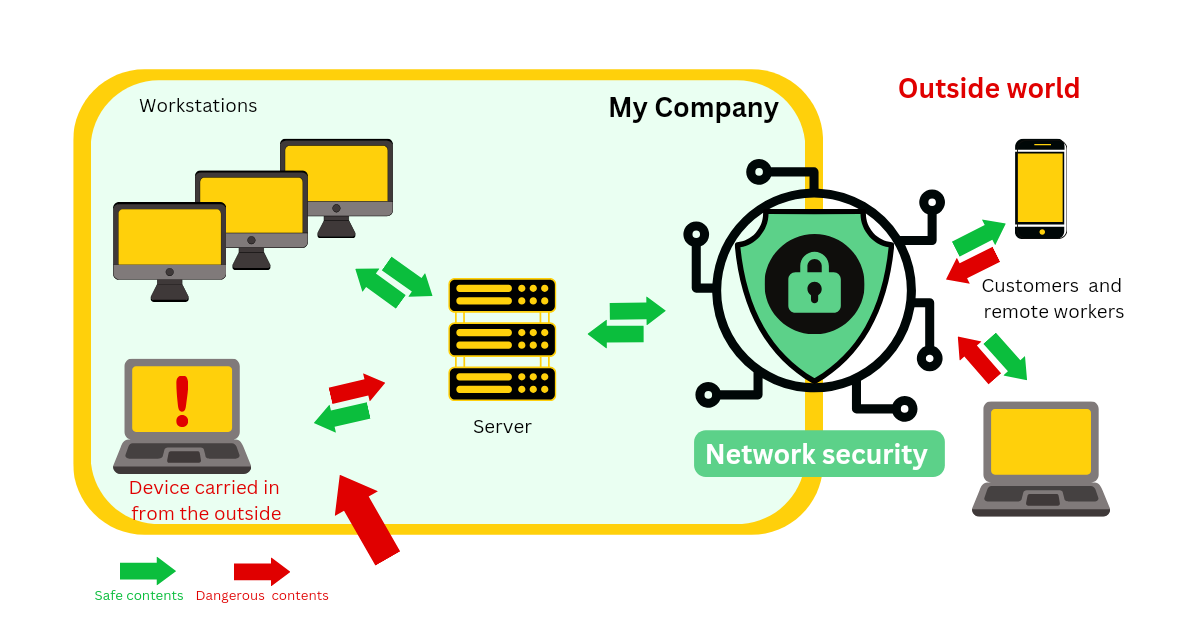
Network security is a multifaceted discipline dedicated to safeguarding the confidentiality, integrity, and availability of data within a computer network. It encompasses a broad spectrum of technologies, processes, and practices designed to defend against unauthorized access, cyber attacks, and data breaches. Essentially, it acts as a digital shield, protecting the vast web of interconnected devices and systems from potential threats.
The Role of Network Security
Guarding Against Cyber Threats
At the forefront of network security’s role is its ability to shield networks from an ever-evolving array of cyber threats. Malicious actors continually seek vulnerabilities to exploit, making it imperative to deploy robust defenses against viruses, malware, and other forms of cyber attacks.
Protecting Sensitive Information
In an age where data is often deemed more valuable than gold, safeguarding sensitive information is non-negotiable. Network security plays a crucial role in ensuring that confidential data, such as customer information and proprietary business data, remains out of the reach of unauthorized entities.
Preserving Network Integrity
Network integrity is the backbone of a seamless and reliable digital infrastructure. Network security measures are implemented to prevent unauthorized modifications to data, ensuring that the information circulating within the network is accurate and trustworthy.
Key Components of Network Security
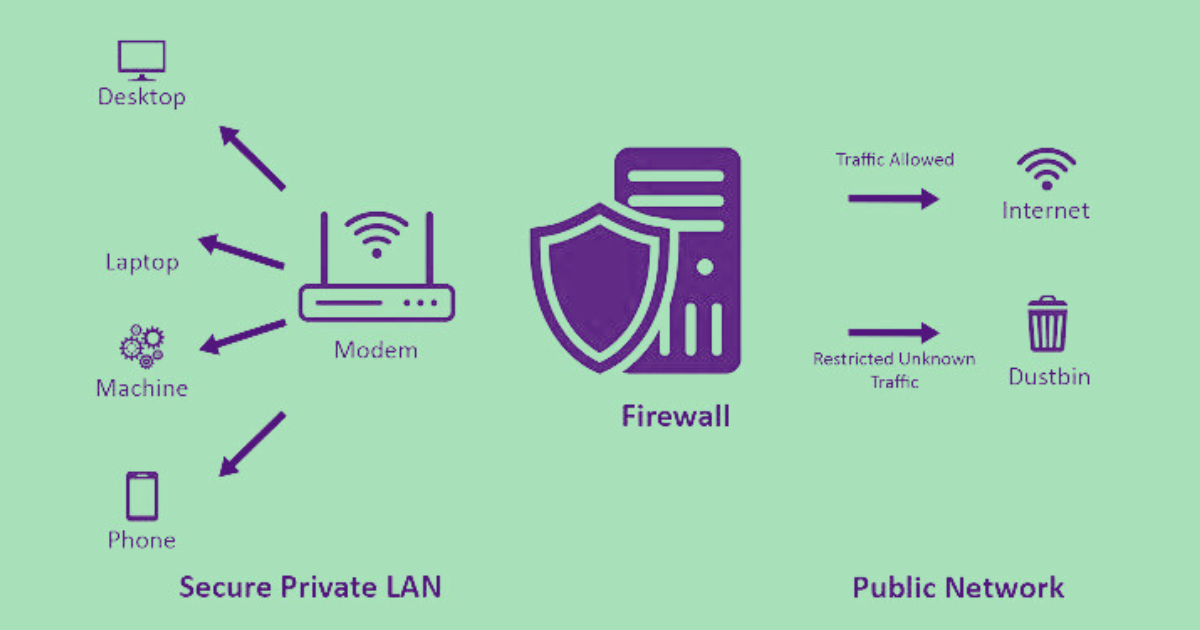
Firewalls as Gatekeepers
Firewalls act as virtual gatekeepers, monitoring and controlling incoming and outgoing network traffic based on predetermined security rules. They serve as a barrier between trusted internal networks and untrusted external networks, preventing malicious entities from infiltrating the system.
Intrusion Detection and Prevention Systems (IDPS)
Network security is proactive in nature, employing Intrusion Detection and Prevention Systems to identify and mitigate potential threats in real-time. These systems analyze network and system activities, raising alarms or taking preventive actions when suspicious behavior is detected.
Encryption Technologies
The use of encryption technologies adds an extra layer of protection by encoding data in a way that can only be deciphered by authorized parties. This ensures that even if data is intercepted, it remains unreadable and secure.
Securing Wireless Networks
With the proliferation of wireless technologies, securing Wi-Fi networks is paramount. Network security protocols, such as WPA3 (Wi-Fi Protected Access 3), ensure that wireless communications remain encrypted and shielded from unauthorized access.
Access Control Mechanisms
Managing and controlling user access is vital to network security. Access control mechanisms, including strong authentication protocols and authorization processes, limit access to sensitive data only to those who are authorized.
Virtual Private Networks (VPNs)
In an era where remote work is becoming increasingly prevalent, VPNs play a crucial role in network security. By creating secure tunnels over the internet, VPNs enable users to access corporate networks securely, safeguarding sensitive data from potential eavesdropping.
As technology advances, so too do the tactics employed by cybercriminals. Thus, the landscape of network security is in a perpetual state of evolution. Continuous monitoring, regular updates, and staying abreast of the latest cybersecurity trends are imperative to maintain the efficacy of network security measures.
Network security stands as the guardian of the digital realm, shielding networks from the ever-present threats that lurk in the virtual shadows. By understanding its pivotal role and adopting a proactive approach to cybersecurity, businesses and individuals can navigate the digital landscape with confidence, knowing that their networks are fortified against potential breaches and cyber attacks. In this era of connectivity, network security is not merely a choice but a necessity for those seeking a secure and resilient digital presence.
In the vast and ever-evolving landscape of the internet, concerns about privacy and security have become more pronounced than ever. As we traverse the digital realm, our online activities are under constant scrutiny, making the role of an IP hider indispensable. Let’s delve into the fundamentals of IP hiders, understanding their significance in safeguarding your online presence and ensuring a secure and anonymous browsing experience.
What is an IP Hider and How Does it Work?
An IP hider, or IP address hider, serves as a shield for your online identity by concealing your true IP address, the unique identifier assigned to your device when connected to the internet. This digital fingerprint reveals your location, browsing habits, and sensitive information. The ingenious functionality of an IP hider lies in rerouting your internet traffic through a virtual private network (VPN) or proxy server, effectively masking your real IP address and providing you with an anonymous online persona.
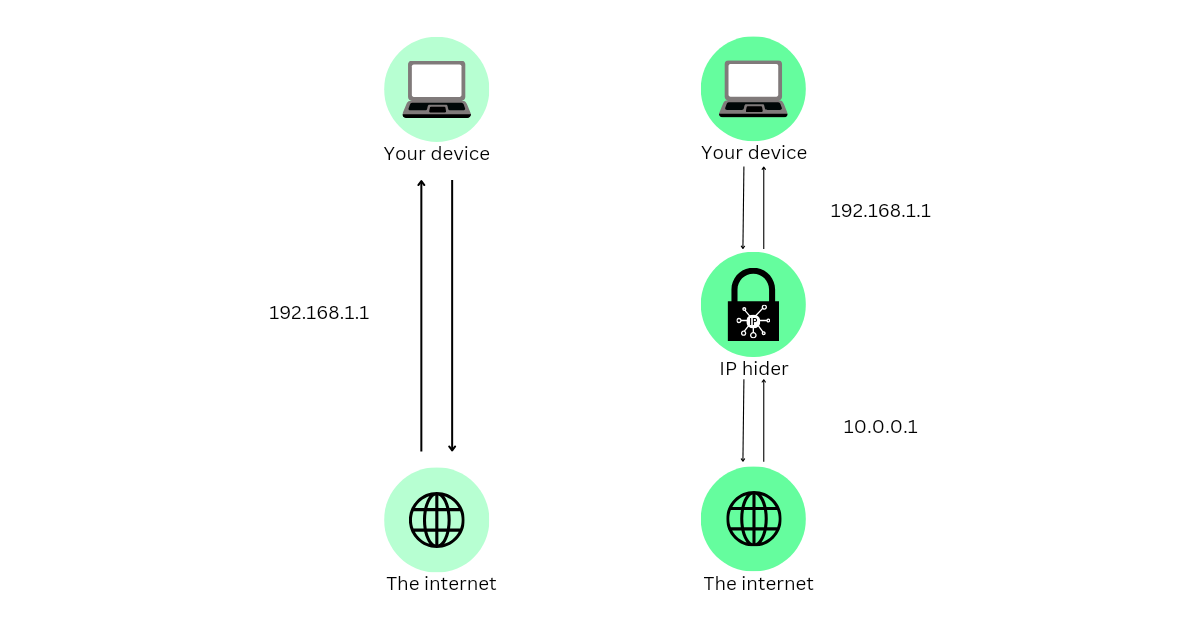
The Crucial Role of an IP Hider in Protecting Your Privacy
Anonymous Browsing
At the forefront of its capabilities, an IP hider enables you to browse the internet without leaving a digital trail. This anonymity is pivotal in an age where data breaches and cyber threats are rampant.
Bypassing Geo-Restrictions
Imagine having the freedom to access region-restricted content effortlessly. An IP hider empowers users to do just that by allowing them to connect to servers in different locations, providing a seamless and global internet experience.
Enhanced Security
In an era dominated by cybersecurity concerns, an IP hider acts as a guardian for your online security. By encrypting your internet traffic, it adds an extra layer of protection, shielding you from potential hackers, identity thieves, and other malicious entities.
Securing Public Wi-Fi Connections
Public Wi-Fi networks, often a breeding ground for cyber attacks, become safer havens with an IP hider. By encrypting your connection, this tool safeguards your data from potential eavesdroppers on the same network, ensuring your peace of mind while on the go.
Preserving Online Freedom
For those facing internet censorship, an IP hider becomes a beacon of hope. By providing access to blocked websites and services without fear of reprisal, it becomes a crucial tool for preserving online freedom.
Choosing the Right IP Hider for Your Needs
Selecting the ideal IP hider involves considering essential factors such as server locations, connection speed, and encryption protocols. Look for a reliable VPN service that offers a user-friendly interface, multiple server locations, and robust security features to ensure comprehensive protection for your online journey.
The role of an IP hider in today’s digital age is pivotal for those seeking a secure, anonymous, and unrestricted online experience. Whether you’re prioritizing privacy, concerned about cybersecurity, or aiming to access region-restricted content, an IP hider provides a valuable solution. By concealing your IP address and encrypting your internet traffic, these tools empower users to navigate the online world with confidence, ensuring a private, secure, and unrestricted internet experience. Embrace the power of IP hiders and take control of your digital presence.
In the ever-evolving terrain of cyberspace, where the digital realm intertwines with our daily lives, the
need for robust cybersecurity measures has never been more critical. Among the frontline defenders in
this digital battleground is the firewall, a stalwart guardian that secures networks and thwart potential
cyber threats.
Understanding the Firewall
A firewall acts as a virtual barrier between your computer or network and the vast expanse of the
internet. Just as a physical firewall prevents the spread of fire, its digital counterpart is designed to
inhibit unauthorized access, monitor outgoing and incoming network traffic, and allow or block data
packets based on pre-established security rules.
Preventing Unauthorized Access
One of the primary functions of a firewall is to act as a gatekeeper, diligently scrutinizing incoming and
outgoing data packets to determine their legitimacy. This first line of defense prevents unauthorized
access attempts and safeguards sensitive information from falling into the wrong hands. By establishing
a secure barrier, firewalls create a virtual shield that deters cybercriminals and malicious entities.
Strategic Filtering
Firewalls employ a multifaceted approach to filter network traffic, mitigating potential threats before
they can infiltrate your system. They utilize a combination of predefined rules, such as access control
lists and port-based filtering, to discern between legitimate and suspicious data. Additionally, modern
firewalls often incorporate advanced technologies like deep packet inspection and intrusion detection
systems, providing an extra layer of defense against sophisticated cyber threats.
Adaptive Security Measures
The threats constantly evolve, demanding adaptive security measures. Firewalls rise to this challenge by
dynamically adjusting their security protocols to counter emerging threats. This real-time
responsiveness ensures that your digital fortress remains resilient against the latest cyber adversaries,
providing a proactive defense mechanism.
Network Segmentation: Enhancing Defense Strategies
Firewalls play a crucial role in implementing network segmentation, a practice that involves dividing a
network into distinct segments. By compartmentalizing network resources, firewalls reduce the
potential impact of a security breach. This not only limits the lateral movement of attackers within a
network but also enables more focused monitoring and control over specific areas, fortifying the overall
cybersecurity posture.
Allowing Legitimate Traffic
While the primary function of a firewall is to block unauthorized access and malicious activities, it also
recognizes the importance of facilitating legitimate traffic. Transitioning smoothly between restrictive
and permissive modes, firewalls strike a delicate balance, ensuring that essential data and
communications flow seamlessly while maintaining a robust defense against potential threats.
In the ever-expanding digital ecosystem, where cyber threats loom large, firewalls stand as stalwart
guardians, fortifying our digital infrastructure. Their multifaceted approach, adaptive capabilities, and
strategic filtering mechanisms make them indispensable in the ongoing battle against cyber adversaries.
In today’s wild west of the internet, we’re all just trying to dodge the cyber bullets, and one of the sneakiest out there is ransomware. Imagine waking up to find all your files held hostage until you pay up – sounds like a nightmare, right? That’s where our digital superhero, anti-ransomware, swoops in to save the day.
Getting to Know the Sneaky Villain: Ransomware
Picture this: you innocently click on a link, and boom – your files are kidnapped by ransomware. They’re all locked up, and the bad guys are demanding a ransom. It’s like a digital hostage situation, and no one wants to be caught in that mess.
Why We Need Anti-Ransomware as Our Shield
Enter anti-ransomware, the guardian angel of your digital world. Unlike those antivirus tools that only recognize known bad guys, anti-ransomware is like having a security guard on steroids. It watches for any signs of trouble and kicks those cyber bullies to the curb before they can even think about causing chaos.
Being a Proactive Defender
Anti-ransomware doesn’t wait for trouble – it stops it in its tracks. By keeping a close eye on how your system behaves, it can sniff out ransomware patterns and shut them down. This means you can sleep peacefully without worrying about waking up to a digital disaster.
Always On Guard: Real-time Protection
Cyber threats are like sneaky ninjas, always trying to find new ways to attack. That’s why anti-ransomware is a 24/7 bodyguard for your digital stuff. It’s constantly updating its knowledge to stay one step ahead of the latest tricks. You can think of it as your personal cyber superhero, always ready to jump into action.
Getting Your Stuff Back: The Heroic Recovery
Even if, heaven forbid, ransomware does manage to sneak in, anti-ransomware has a backup plan. Many of these tools come with a superpower – they can help you recover your files without paying the ransom. It’s like having a get-out-of-jail-free card in the digital world.
In the crazy world of cyber threats, anti-ransomware is your digital superhero, standing tall against the bad guys. It’s the friend you want by your side, always watching your back, so you can surf the web without fear. So, gear up, fortify your digital castle, and let anti-ransomware be the hero in your digital story.
Not all anti-ransomware tools are created equal, so choose wisely. Look for one that’s easy to use, plays well with your other security tools, and can defeat the latest cyber threats. Think of it as finding a trustworthy sidekick to help you navigate the digital frontier.
Ever wondered how your messages, passwords, and cat memes stay safe while zooming through the vast internet space? Enter encryption- Your digital secret agent! Let’s dive into the cool world of encryption and see how it’s like having a secret agent protecting your online life.
What’s an Encryption?
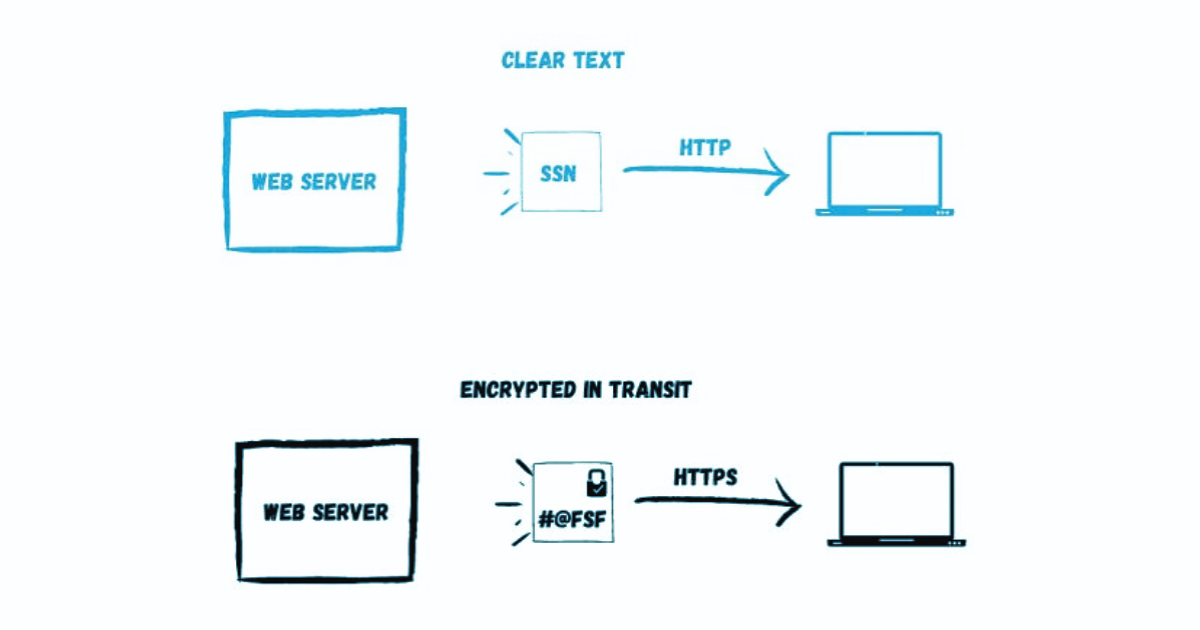
Encryption, at its core, is like turning a message into a secret code only a select few can understand. It transforms plain, understandable data into an unreadable format known as ciphertext, using cryptographic algorithms. Think of it as creating a secret language that only those with the right key can decipher, ensuring that unauthorized entities cannot gain access to sensitive data.
The Role of Encryption
Encryption plays a crucial role in safeguarding our digital communications, whether it’s a private message, an online purchase, or accessing your bank account. It acts as a digital shield, protecting your information from prying eyes. Transport Layer Security (TLS) and Secure Sockets Layer (SSL) protocols, commonly seen as https:// in website URLs, encrypt the data exchanged between your device and the server, thwarting potential eavesdroppers and hackers.
In the realm of email communication, end-to-end encryption has become increasingly crucial. Services like ProtonMail and Signal employ this type of encryption, ensuring that only the intended recipient can decipher the message. This adds an extra layer of protection, especially in an age where cyber threats are omnipresent.
Data Storage
Encryption doesn’t stop at protecting information in transit; it extends its reach to safeguarding stored data as well. Full Disk Encryption (FDE) and File-Level Encryption (FLE) are methodologies employed to encrypt entire storage devices or specific files, respectively. This means that even if an unauthorized user gains physical access to your device or cloud storage, they would encounter nothing but an unintelligible jumble without the decryption key.
Navigating a Privacy-Focused World
In a world where privacy concerns are on the rise, encryption has emerged as a beacon of trust for users seeking confidentiality in their digital interactions. Virtual Private Networks (VPNs), for example, use encryption to create secure tunnels, ensuring that your internet traffic remains private and protected from potential eavesdroppers, such as government agencies or malicious hackers.
The Battle Against Cybercrime: Encryption as the Guardian of Confidentiality
The digital landscape is fraught with threats, from ransomware attacks to identity theft. Encryption serves as a formidable ally in the ongoing battle against cybercrime. By encrypting sensitive information, individuals and organizations can mitigate the risks associated with data breaches, protecting both personal and proprietary data from falling into the wrong hand.
In a world where information is a valuable currency, encryption stands as the guardian of our digital realm. From securing online transactions to protecting stored data and fortifying communication channels, its role is irreplaceable. As we continue to navigate the vast landscape of the internet, understanding and embracing encryption is not just a choice but a necessity, empowering us to take control of our digital future with confidence and security.
In the vast landscape of the internet, where communication and information flow freely, the omnipresence of spam threatens to disrupt the seamless online experience we all crave. In this digital age, where our inboxes are flooded with countless emails and our social media feeds are cluttered with unsolicited content, the importance of anti-spam measures cannot be overstated. Let’s get familiar with anti-spam and unravel its crucial role in preserving the integrity of our online interactions.
Know the Menace: Spam
Before we explore the solutions, it’s essential to grasp the gravity of the spam problem. Spam, in its various forms, includes unsolicited emails, unwanted advertisements, and malicious messages that can infiltrate our digital lives. Apart from being a nuisance, spam poses serious threats such as phishing attacks, identity theft, and the spread of malware. As users, we need a shield to protect ourselves from these digital predators.
Understanding Anti-Spam
Anti-spam is a set of technologies and strategies designed to mitigate and prevent the influx of unwanted or malicious electronic messages, commonly known as spam.
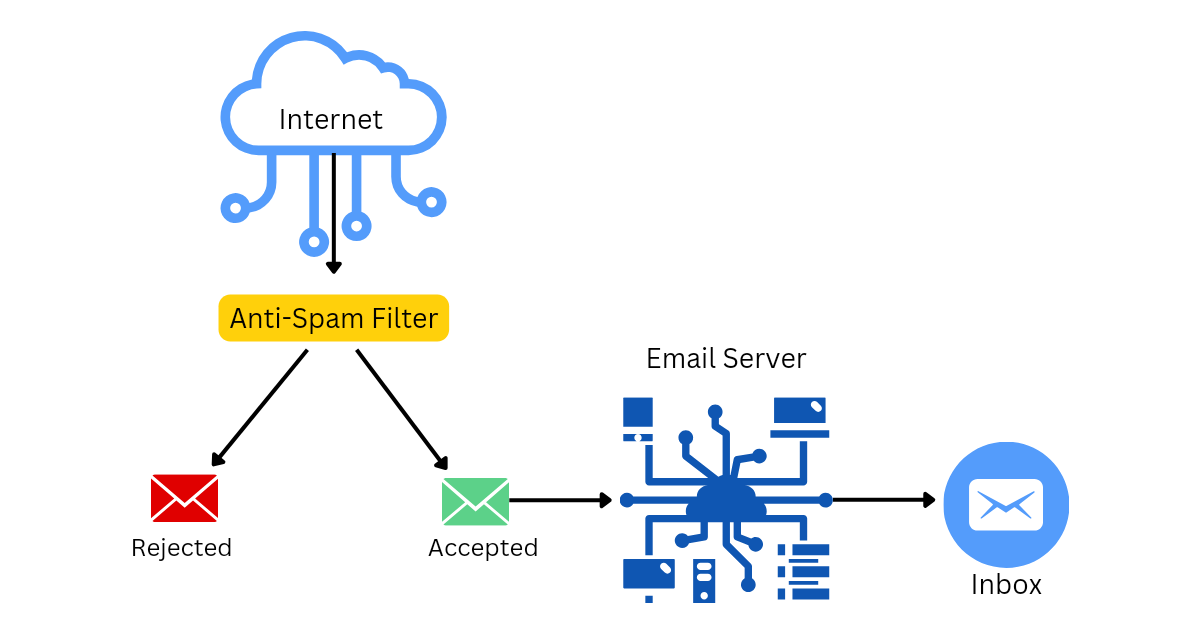
The Role of Anti-Spam Measures
Filtering Algorithms
Anti-spam measures deploy sophisticated filtering algorithms that scrutinize incoming emails and messages. These algorithms are designed to distinguish between legitimate communications and spam, ensuring that only relevant and safe content reaches our inboxes.
Email Authentication Protocols
A crucial aspect of anti-spam efforts involves implementing email authentication protocols like SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail). These protocols verify the legitimacy of the sender, mitigating the risk of phishing attacks and email spoofing.
Machine Learning Technologies
Leveraging the power of machine learning, anti-spam solutions continuously evolve to adapt to new spamming techniques. By analyzing patterns and learning from user behavior, these technologies enhance their ability to identify and block spam, providing a proactive defense against emerging threats.
The Impact on User Experience
Implementing robust anti-spam measures has a direct and positive impact on the overall user experience. Users can enjoy a clutter-free inbox, devoid of irrelevant and potentially harmful content. This streamlined communication environment fosters trust and confidence in online interactions, encouraging users to engage more freely without the constant fear of falling prey to cyber threats.
User Education and Awareness
Anti-spam measures go beyond technological solutions; they also include user education initiatives. By raising awareness about phishing tactics and promoting good online hygiene, users become more equipped to identify and avoid falling victim to spam-related scams.
In the ever-expanding digital realm, where connectivity is key, the battle against spam is a continuous effort. Anti-spam measures play a pivotal role in creating a secure and enjoyable online environment for users. From advanced filtering algorithms to cutting-edge machine learning technologies, these measures form a comprehensive defense against the multifaceted threats posed by spam. As we navigate the digital jungle, let us embrace and appreciate the significance of anti-spam solutions, ensuring that our online experiences remain both enriching and secure.
Cyber threats loom large, with malicious actors constantly devising new ways to compromise our
sensitive information. In this digital battleground, one unsung hero plays an important role in enhancing
our defenses – Anti-Spyware.
Understanding Spyware
Before delving into the significance of Anti-Spyware, it’s essential to grasp the nature of the enemy it
combats – spyware. Spyware is a clandestine software that infiltrates devices with the intent of covertly
gathering information. This can range from keystrokes and login credentials to personal and financial
data. The insidious nature of spyware lies in its ability to operate surreptitiously, often without the
user’s knowledge, making it a formidable foe in the realm of cybersecurity.
The Silent Invader
Transitioning from traditional cyber threats to modern-day spyware is seamless, catching even the most
vigilant users off guard. It often piggybacks on seemingly innocuous downloads or lurks in the shadows
of malicious websites. Once embedded in a system, spyware can wreak havoc, compromising not just
personal data but also the overall integrity and performance of the device.
Role of Anti-Spyware
In this cyber arms race, Anti-Spyware emerges as the stalwart defender against the stealthy advances of
spyware. Acting as a digital protector, Anti-Spyware is designed to detect, quarantine, and eliminate
spyware before it can inflict damage. Its multifaceted approach involves real-time monitoring, heuristic
analysis, and signature-based detection, ensuring comprehensive protection against both known and
emerging threats.
Real-Time Surveillance
One of the key features that set Anti-Spyware apart is its ability to provide real-time vigilance. Unlike
traditional antivirus solutions that primarily focus on known threats, Anti-Spyware operates proactively.
It constantly monitors system activities, flagging any suspicious behavior that aligns with the
characteristics of spyware. This real-time scrutiny is invaluable in preventing zero-day attacks, where
cyber threats exploit vulnerabilities before they are officially recognized.
Heuristic Analysis
Anti-Spyware leverages heuristic analysis, a sophisticated method that goes beyond predefined
signatures. By understanding the behavioral patterns of spyware, even those not previously identified,
heuristic analysis enables Anti-Spyware to identify and neutralize emerging threats. This forward-
thinking approach is pivotal in the ever-evolving landscape of cyber threats.
Signature-Based Detection
While heuristic analysis is forward-looking, Anti-Spyware also employs signature-based detection to
recognize known spyware variants. Regular updates ensure that the software remains armed with the
latest threat intelligence, providing a robust line of defense against well-established malicious codes.
The Holistic Defense
What makes Anti-Spyware superior is its holistic defense mechanism. It doesn’t merely focus on
spyware; it complements other cybersecurity measures, creating a comprehensive shield against a
spectrum of digital threats. This synergy enhances overall cybersecurity resilience, making Anti-Spyware
an integral component of any robust defense strategy.
In the complex domain of cybersecurity , where the stakes are higher than ever, Anti-Spyware emerges
as a linchpin in safeguarding our digital existence. Its ability to adapt, anticipate, and neutralize threats
positions it as a cornerstone in the ongoing battle against cyber menaces. Let Anti-Spyware be your
shield and ensure a secure and resilient cyberspace.
In an era dominated by digitization, the omnipresence of technology has ushered in unprecedented conveniences but has also exposed us to evolving threats. As businesses and individuals alike embrace the digital landscape, the need for robust cybersecurity measures has become more paramount than ever. At the forefront of this battle against cyber threats stands Artificial Intelligence (AI) Security, a revolutionary paradigm that is reshaping the way we defend our digital assets.
The Rising Tide of Cyber Threats
Cyber threats have morphed into sophisticated and dynamic entities, constantly adapting to exploit vulnerabilities in our digital infrastructure. Traditional cybersecurity measures, while effective to a certain extent, often fall short in addressing the intricacies of modern cyber attacks. This is where AI steps in, leveraging its prowess to not just react but proactively anticipate and neutralize threats.
Proactive Defense
Unlike conventional security systems that operate on predefined rules, AI Security operates on a proactive model. Through the utilization of advanced algorithms and machine learning, AI can analyze vast amounts of data to identify patterns and anomalies that might signify a potential threat. This proactive stance allows organizations to stay one step ahead of cybercriminals, thwarting attacks before they can cause harm.
Machine Learning: A Dynamic Shield Against Evolving Threats
One of the cornerstones of AI Security is machine learning, a subset of AI that enables systems to learn and adapt without explicit programming. In the realm of cybersecurity, this translates to systems that can autonomously improve their threat detection capabilities over time. As cyber threats evolve, AI systems equipped with machine learning can quickly adapt, fortifying defenses against emerging risks.
Enhanced Endpoint Security: A Shield for Every Device
Endpoints, including computers, smartphones, and IoT devices, serve as gateways for cyber attacks. AI Security excels in providing enhanced endpoint security by constantly monitoring and analyzing device behavior. This allows the system to identify deviations from normal patterns and promptly flag potential security breaches, preventing unauthorized access and data compromise.
Thwarting Insider Threats: Identifying the Unseen Foe
While external threats often take the spotlight, insider threats pose a significant risk. Whether intentional or accidental, employees can inadvertently become conduits for cyber attacks. AI Security employs behavioral analytics to monitor user activities, detecting unusual patterns that may indicate malicious intent. By identifying insider threats in real-time, organizations can safeguard sensitive information and maintain the integrity of their digital ecosystem.
Adaptive Authentication: Fortifying Access Controls
Authentication is the first line of defense in cybersecurity. AI Security introduces adaptive authentication, a dynamic approach that evaluates the risk associated with each login attempt. By analyzing user behavior, location, and other contextual factors, adaptive authentication ensures that access controls evolve in response to changing threat landscapes, reducing the likelihood of unauthorized access.
As cyber threats continue to evolve, so must our defense mechanisms. AI Security is not a static solution but a dynamic force that evolves alongside the ever-changing digital landscape. The integration of AI into cybersecurity strategies signifies a paradigm shift, where intelligent algorithms and self-learning systems play a pivotal role in fortifying our digital frontier.
The synergy between AI and cybersecurity is pivotal in safeguarding our digital existence. By embracing AI Security, organizations empower themselves with a proactive defense mechanism that adapts to the relentless evolution of cyber threats. As we navigate the intricate web of the digital world, the role of AI in cybersecurity stands as a beacon of innovation, offering a resilient shield against the ever-present specter of cyber threats.
In the fast-paced, digitally-driven landscape we navigate today, the security of our personal and professional information is a paramount concern. As we immerse ourselves in the convenience of technology, the lurking threat of cybercrime demands our attention. Whether you’re a casual internet user or a business navigating the digital domain, antivirus software is your first line of defense. Antivirus software is the unsung hero in the battle against malicious digital invaders.
Antivirus software or anti-malware software is a specialized program designed to detect, prevent, and remove malicious software (malware) from computer systems, networks, and digital devices.
Let’s explore why antivirus protection is not just a luxury but a necessity in our interconnected world.
Guardian of the Digital Gate
Antivirus software, our digital shield, stands guard against a myriad of online threats, particularly viruses. This cybernetic superhero is designed to detect, prevent, and eliminate harmful programs before they compromise the integrity of our digital lives.
Real-Time Vigilance
Picture this: a vigilant guardian constantly patrolling your digital space. Antivirus software operates in real-time, scrutinizing your device for any signs of malicious activity. The moment it detects a potential threat, it springs into action, swiftly isolating the infected files or eradicating the danger altogether. This proactive approach is key to preventing malware from establishing a stronghold on your system.
Up-to-Date Armor
In the ever-evolving arms race between cybercriminals and cybersecurity, regular updates are the secret weapon. Antivirus software providers release updates containing the latest virus definitions and security patches. Keeping your antivirus software up-to-date ensures that it remains a formidable opponent against emerging threats, providing a continuously reinforced defense.
Beyond Malware Defense
Antivirus software isn’t just about repelling malware. Modern solutions often come bundled with additional features like firewalls, phishing protection, and identity theft prevention. These supplementary tools enhance your overall digital security, creating a comprehensive defense against a diverse range of cyber threats.
Holistic Cybersecurity
While antivirus software is a vital component, a holistic approach to cybersecurity is imperative. Responsible online behavior, such as cautious email interactions and avoiding dubious links, complements the protective role of antivirus software. It’s a combined effort where user awareness and digital guardianship work hand-in-hand.
Business Armor
In the corporate arena, where the stakes are higher, antivirus solutions become mission-critical. Robust antivirus suites with centralized management become the backbone of an organization’s cybersecurity strategy. This centralized control ensures uniform security standards across all devices, protecting the integrity of valuable business data.
In the complex realm of cybersecurity, antivirus software emerges as a reliable partner, offering more than just protection—it provides peace of mind. By investing in a robust antivirus solution, cultivating responsible online habits, and embracing a holistic approach to cybersecurity, individuals and businesses can fortify their defenses against the ever-evolving landscape of cyber threats. In the realm of digital security, prevention isn’t just better than a cure; it’s the cornerstone of a secure and interconnected future.
About Us
Welcome to Ultracare Technology, where cybersecurity meets innovation! Embark on a unique journey through our digital realm, dedicated to unraveling the secrets of cybersecurity. Navigate the intricate web of online threats with our exclusive insights, revealing the latest in cybersecurity technologies and software. From futuristic defenses to ingenious solutions, Ultracare Technology is your avant-garde guide to securing the digital frontier. Immerse yourself in curated content that transcends conventional wisdom, empowering you to safeguard your digital world like never before.